Deploying onto AWS is pretty straight forward. The video above has the key steps, but there is a little bit of prep work we need to do. As always, your best bet is the official Attack Range documentation.
Build steps
Since this post is specifically for deploying from Linux, you’ll need a Linux host, I chose Ubuntu 23.04. There are other deployment options, the main other choice I recommend is using a container, and I’ll follow up with a post on that soon.
Install required dependencies
apt-get install -y python3 git unzip python3-pip curl
Install Terraform
wget -O- https://apt.releases.hashicorp.com/gpg | sudo gpg --dearmor -o /usr/share/keyrings/hashicorp-archive-keyring.gpg
echo "deb [signed-by=/usr/share/keyrings/hashicorp-archive-keyring.gpg] https://apt.releases.hashicorp.com $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/hashicorp.list
sudo apt update && sudo apt install terraform
Install Packer
curl -fsSL https://apt.releases.hashicorp.com/gpg | sudo apt-key add -
sudo apt-add-repository "deb [arch=amd64] https://apt.releases.hashicorp.com $(lsb_release -cs) main"
sudo apt-get update && sudo apt-get install packerInstall and configure AWS CLI
apt-get install -y awscli
aws configureInstall Poetry
curl -sSL https://install.python-poetry.org/ | python3 -
sudo nano ~/.profile
`export PATH="/home/YOUR_HOME/.local/bin:$PATH"`
You can then logout and back in
Clone the Attack Range repo
git clone https://github.com/splunk/attack_range.git
cd attack_rangeLaunch Attack Range
poetry shell
poetry install
python attack_range.py configureThis will generate attack_range.yml. You can build from this straight away, I prefer to rename the file and have a few different configurations to use.
cp attack_range.yml aws.ymlYou can then start building
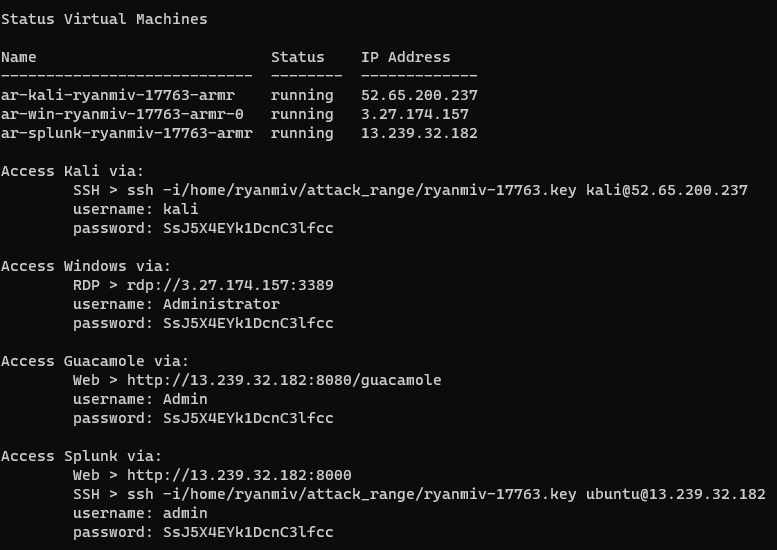
python attack_range.py -c aws.yml buildIn around 30 minutes, you’ll be presented with the status of your lab environment, like below. You can always bring this status page back with python attack_range.py -c aws.yml show